PREFACE

This book is aimed at GCSE students of all ages but primarily those in 14-19 full time education. Furthermore it has been designed to contain the fundamental elements of the WJEC GCSE Short Course in ICT although elements of it may be useful references for other courses, levels and examining boards.
Modern School ICT courses are very demanding on student time regards internal controlled assessment and all too often there is insufficient time for white board or smart board sessions within standard timetabling frameworks for students to acquire a complete set of written revision notes in their own handwriting. The old fashioned copy and learn methods in education still have a tremendous amount going for them but what if there simply isn't time?
Some teachers perhaps assume that because they find GCSE questions 'common sense' that their students will somehow have the same maturity of perception and skills in application and will thus be expected to sit the exam virtually unaided. Their students being carefully trained and prompted to jump through all the necessary practical assessment hoops yet being significantly deficient in theoretical knowledge. This book aims to bridge the gap and provides segments of in brief 'byte size' knowledge following a concise alphabetical definitive pathway through the subject from A-Z and is written in a simple style with phraseology which can be abstracted to meet examiner model answer key phrases.
Chapter One : Computer Health and Safety
At GCSE level a simple understanding of the facts as summarised below is all that is needed.
 Use
good chairs, adjust monitor heights, brightness and refresh rates to
suit individuals. Take regular breaks, get eyes tested regularly.
RF radiation from wireless computers and routers is a bone of
contention. About half of all scientific studies show that
there is no significant biological interaction or health risk whereas
the other half suggest the opposite to be true.
Use
good chairs, adjust monitor heights, brightness and refresh rates to
suit individuals. Take regular breaks, get eyes tested regularly.
RF radiation from wireless computers and routers is a bone of
contention. About half of all scientific studies show that
there is no significant biological interaction or health risk whereas
the other half suggest the opposite to be true.
Certainly, there are recorded instances of some people being 'electro-sensitive' and experiencing burning or tingling feelings of the skin in proximity to such devices. If you are one of these then it may be pertinent to used a traditional hard wired network.
CHAPTER 2
|
Computers & the Law |
Computer users have to obey the law, just like anybody else. Since computers are capable of giving great power to their users, a number of laws apply specifically to them.
The Data Protection Act 1998
The Data Protection Act was written to prevent people from misusing personal data (data that can be used to identify a living individual).
The Computer Misuse Act 1995
The Computer Misuse Act is designed to help deal with the problems of computer hackers and viruses
|
Data Protection Act |
Most businesses have to register as users of personal data. There are exemptions: mainly those who use data for crime prevention, national security, tax collection, or mental health reasons.
The Act has 8 principles, or rules. Data must be:
|
|
1. processed fairly and lawfully 2. used for the lawful purpose it was collected for 3. adequate and relevant to purpose collected for 4. kept accurate and up-to-date 5. kept no longer than necessary 6. processed within the rights of the data subjects 7. kept secure 8. kept only within the EEC |
|
Data Subjects |
Within the Data Protection Act, the people data is about are called data subjects.
Data subjects have a number of rights. These include the right to:
|
1. see data held on them on request. 2. alter inaccurate or incorrect data. 3. sue if data is wrong, and the mistake causes harm to them. |
Data is collected by data controllers. A person called the data commissioner exists to help make sure the Act is followed.
|
Computer Misuse Act |
Aimed at reducing hacking and the threat from viruses, there are 3 main offences covered by the Act:
|
1. Unauthorised access to computer material (hacking). This includes copying software illegally (called software piracy). 2. Gaining unauthorised access to a computer to carry out serious crimes like fraud or blackmail. 3. Unauthorised changing of computer files, including planting viruses and deleting files. |
Conviction for any of the above can lead to an unlimited fine or five years in prison.
|
Copyright Law |
|
Copyright laws apply to material on computer as well as printed work. This means that you must credit any work that you download or copy from other sources. Even then, you may still have broken the law.
This also means that it is illegal to copy computer software without a licence to do so - just as it is illegal to copy entire books without a licence!
Small sections of some books and some software can be copied for educational purposes provided financial gain is not made. It is always best to seek the author’s permission and/or acknowledge the person.
CHAPTER 3
Control Systems
Computer Control Systems are made up of software and hardware that controls other equipment.
They can be "dedicated" systems that perform a set of pre-programmed instructions, or computer controlled ("dynamic") systems that react to input from sensors.
Most control systems use feedback loops to tell them how to behave. This is when information from a sensor (e.g. temperature sensor) is used to decide how to use an output device (e.g. heater).
The output device will have some sort of effect on the next reading from the sensor - e.g. switching on the heater will raise the temperature at the temperature sensor.
Robots a sort of control system
A
robot is an automated piece of equipment designed to carry out
routine repetitive tasks.

They can usually be re-programmed to perform a number of different tasks, for example, spraying different shaped car parts with paint.
Robots are cheaper to operate than paying people wages, but are very expensive to buy.
Robots do not get tired or make mistakes, and can carry out tasks that are dangerous or difficult for humans to do - e.g. travel to Mars!
Robots can learn new tasks in two main ways.
A programmer writes a set of instructions, then watches the robot follow them. The instructions are then improved if needed.
The robot is guided through the task once and produces its own instructions.
|
Control Systems: EPOS |
EPOS stands for Electronic Point of Sale. This is a general name for the computerised tills that you see in shops and supermarkets.
EFTPOS stands for Electronic Funds Transfer at Point of Sale. This is where customers can pay for goods using credit or debit cards.
|
This is how an EPOS system works:
EPOS systems
can be linked to loyalty
card databases or
analysis
software to
help shops p |
Computer Control in Health Care
The main use of computer control in hospitals is in life-support systems.
Sensors attached to a patient monitor:
· pulse
· temperature
· blood pressure
· breathing rate
Readings from sensors are taken at regular intervals and used as input to a computer.
If any of these readings goes outside acceptable levels an output signal sets off an alarm to alert the nursing staff.
Life
Support systems are often used for patients in intensive care
(e.g. after operations) or for prematurely born babies. This type of
system has several advantages:

· monitoring can be continuously done 24 hours a day
· no chance of human errors, e.g. due to tiredness
· frees the nursing staff to carry out other duties
Unfortunately these systems are expensive to buy, and need regular maintenance.
Chapter 4 Databases
Databases are one of the most powerful tools that people use to help them handle large amounts of information.
A database is made up of one or more related files (called tables in Microsoft Access).
A file is made up of one or more related records.
Records are made up of one or more related fields.
A field is made up of a group of related characters. It is a piece of information about something.
Fields can be one of a range of different data types, including: Text, Integer, Real number, Yes/No (Boolean), Date, Time, Sound, and Video.
Key fields allow computers to uniquely identify each record. They contain a unique value for each record. The records in a file are usually sorted by the value of the key field, for example, the ProductID in a stock file.
Each field can only hold one data type at any time. e.g. a field for a date will always, and only, hold a date. Fields can be either fixed or variable in length.
Fixed length fields will always use a certain number of characters for each record. Variable length fields only use the minimum number of characters necessary for each record.
Fixed length fields ( sometimes called truncated fields) are faster to search through, but variable length fields use less storage space.
Example of use of truncated or fixed length ( 5 character) surname field in a database.
Adamonson : Adamo
Dickinson : Dicki
Cuthbertson : Cuthb
Coding Databases
A well-designed database will code data that appears many times, rather than entering full terms.
e.g. in a database that records the gender of a person, it would be sensible to code as "M" or "F" rather than typing "Male" or "Female" each time. M/F coding which has only two possible choices is also called BOOLEAN
This also allows you to enter data much faster, as well as allowing you to easily validate the input.
Databases can be searched by creating a query, of which there are two types: simple and complex.
A simple query uses one test on a single field to find records in a database. They are made up of three parts: a field name, an operator, and a value.
Examples of operators are equal to (=), more than (>), less than (<), and not equal to (<>).
An
example of a simple query is:
Colour
=
Red
Complex queries use more than one test, or look at more than one field. They are made up of two or more simple queries joined together by logical operators, such as AND, OR and NOT.
An example of a complex query is:
Colour
=
Red
OR
Colour
=
Blue
Databases consist of 1 or more files (or tables). Files are made up of records.
Records consist of 1 or more fields, basically information about something.
Key fields make a record unique, e.g. a customer number.
Fields contain different data types including Text, Integer, Real number, Yes/No (Boolean), Date, Time, Sound, and Video
Fields can be fixed or variable length. Fixed length fields search faster; variable fields take up less disk space.
Coding data speeds up data entry and helps avoid mistakes. e.g. instead of entering child or adult, code as c and a in the appropriate field.
Databases are searched with simple or complex queries. Simple queries search on a single field. Complex queries can search more than one field on a combination of terms.
When a new member
joins a library, a membership card is issued which has a
barcode printed on it. Every book in the library also has a
barcode printed inside it.
When a member takes a book out on loan, the barcode of the book is read by a barcode reader. So too is the barcode on the member's card. Together with the date, this makes up a transaction. Input: book's and member's barcode, date, librarian's name, etc. This transaction is then stored in the library's database. N.B. Barcodes contain a check digit which is used for automatic validation by the barcode reader.
Library Databases |
The library's database would have files (tables) containing details about the:
books, magazines etc..
members
transactions.
Information Retrieval: Librarians need to be able to find out whether books are currently in stock or out on loan - searches have to be performed on the database.
There may also be a link to other libraries so that if a title is available there, it can be requested and transferred between libraries.
Process: The computer system will need to be able to calculate which books are overdue and whether any fines are due. Output: Summary reports, results of searches.
Library systems work in real-time as data is updated immediately books are loaned.
CHAPTER 5
Datalogging and Simulations
Definition: Simulations software represents real-life situations using a computer.
Computer simulations allow people to investigate ideas that would be considered too dangerous or expensive to do in the real world.
Simulations require powerful hardware and complex programming. As the software imitates unknown things, it may not be entirely accurate.
Typical computer simulations include:
Virtual Reality programs like flight-simulators or 3D home-design.
Prediction software, such as Lottery number-choosing.
Models to predict traffic flow on a new road.
· Definition: Data logging systems record data from one or more inputs and stores it on computer. The inputs can be sensors (e.g. temperature), or other input devices such as a keyboard or mouse.
· Data logging systems usually store the data collected in a spreadsheet. This allows users to produce graphs and charts based on the data collected.
· It also allows them to produce statistics such as average values over a period of time, e.g. average rainfall for the last 12 hours.
· Data logging systems usually collect data at regular intervals.
· Examples of datalogging in everyday use include weather stations, and traffic flow systems (the blue cameras by the side of main roads).
· These systems all work 24 hours a day, 7 days a week, and only stop occasionally for maintenance work.
· Data logging systems can work in almost all locations, including many where humans cannot operate safely, e.g. the bottom of the sea, or inside a nuclear reactor.
·
Data logging systems
can be used to provide feedback
to control systems
that operate other devices.
e.g. a greenhouse
might have a system
to monitor
temperature that
also controls
the heaters or
ventilation.
Datalogging systems record data from input devices (sensors) and store it on computer.
Simulations software represent real-life situations on a computer.
Datalogging takes place at regular intervals and can be analysed as graphs, etc.
CHAPTER 6
Expert Systems
These are programs that mimic the intelligence of a human expert in a specific field of knowledge or experience.
They are often used when experts are not easily available, or are too expensive, e.g. to give medical advice.
This works by using a database of stored information on computer about medical conditions. An expert gives the computer a set of rules to use when making a diagnosis.
|
Expert Diagnosis |
When the computer "meets" a patient, it asks a series of questions to help it follow the rules it has been given, until it has enough information to make a "diagnosis". Often the diagnosis
is made on the balance of probability as such we say that 'Fuzzy Logic' has been employed.
Expert systems will only use the rules they have been given to reach a conclusion. They are not usually able to adapt themselves. However, there is interest in using parallel processing systems with back propagation to bridge this gap.
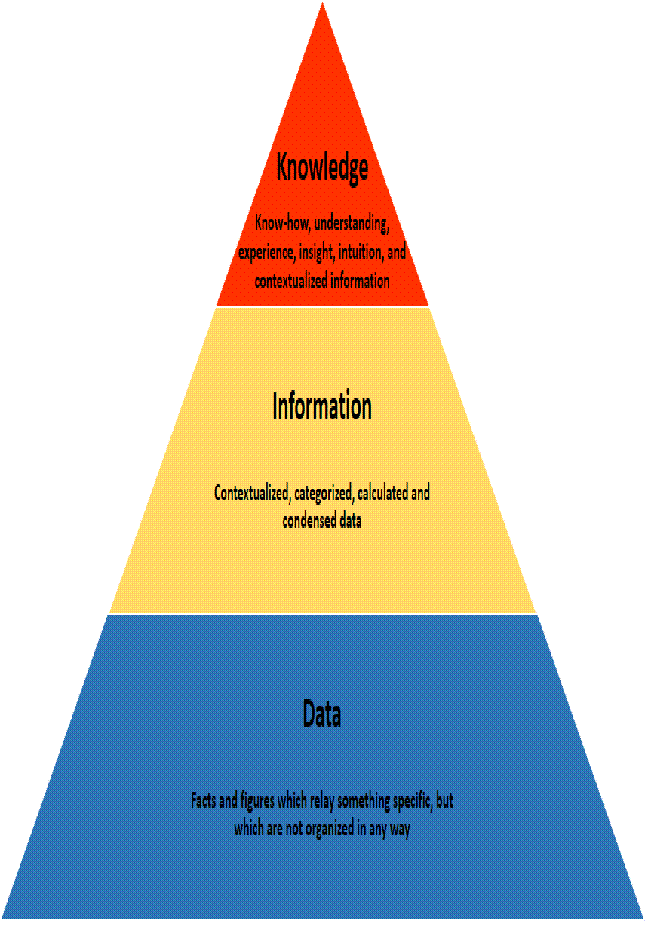
Chapter 7 : Data ,information and Knowledge
Data
Data is processed by computers, the resulting information can then be used to make decisions. You need to know the definitions of data and information and the relationship between the two.
A definition of data
Data is words, numbers, dates, images, sounds etc without context.
For example below is a list of data items:
· 42
· rabbits
· 16:00
· 76
· apples
· 09743245530
· £40
· seaside
Data items need to be part of a structure, such as a sentence, in order to give them meaning.
Information
Information is a collection of words, numbers, dates, images, sounds etc put into context, ie to give them meaning. When used to form part of a sentence they gain meaning:
· There are 42 apples in that box and each one of them has been nibbled by rabbits.
· The fare to the seaside is £40 and the journey takes 73 minutes by rail.
· My telephone number is 09743245531 Call me at 16:50.
This is information - data put into context.
Changing data into information
A structure is needed in order for data to become information. In the table below the second and third columns contain either 'Yes' or 'No' but without headings there is no meaning.
In the table below the second and third columns contain either 'Yes' or 'No' but without headings there is no meaning.
|
Steve |
Yes |
|
|
Jabal |
Yes |
|
|
Adam |
Yes |
|
|
Kieran |
Yes |
|
|
Dylan |
Yes |
|
|
Sophie |
No |
Yes |
|
Maximus |
No |
No |
By adding headings, the data becomes information.
|
Student name |
Present |
Absence authorised |
|
Steve |
Yes |
|
|
Jabal |
Yes |
|
|
Adam |
Yes |
|
|
Kieran |
Yes |
|
|
Dylan |
Yes |
|
|
Sophie |
No |
Yes |
|
Maximus |
No |
No |
Other data sources

A barcode can be read by barcode scanners
Input devices can collect data automatically, eg sensors that continually measure a temperature or a fix-mount barcode reader at a till.
In both of these cases the data collected will be read into a database for processing. With a structure in place (the database) the data becomes information.
Spreadsheets are commonly used to turn data into information.
Knowledge
Knowledge is the ability to understand information and to then form judgements, opinions, make predictions and decisions based on that understanding.
Knowledge from information
Example 1
Each year, for the past five years, the apple crop in Somerset has grown by 10%. The same amount of growth is predicted this year so we need to find markets for a further 10% of apples.
In this example data collected each year, for the past five years, has become information and a pattern in the growth of the apple crop has been identified - 10% year on year. This information has been used to predict the same level of growth this year and has highlighted the need for more markets. The prediction and realisation are knowledge, ie the use of information.
Example 2
The car looked like it had flat tyres and it had a pool of petrol underneath it at the back. There was smoke coming from the bonnet. I took the decision not to allow anyone near it and to evacuate the area.
In this example the judgement made and the decision that followed, i.e. to evacuate the area, is the knowledge, gained after assessing the available information.
Thus Data leads to information, and information leads to knowledge.
Chapter 8 'GIS' Geographical INFORMATION systems
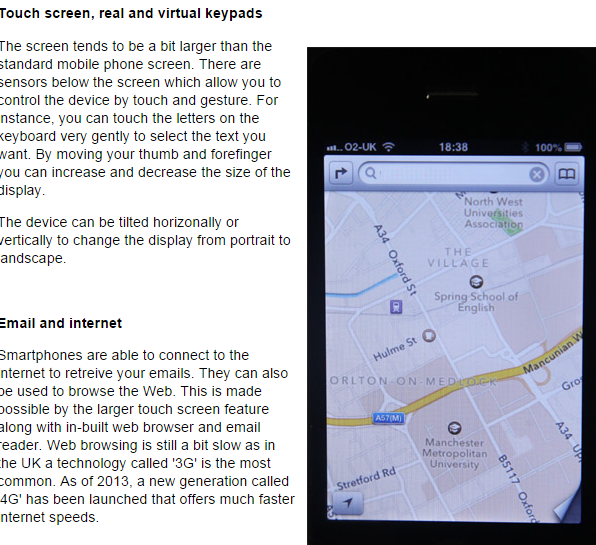
Geographers have traditionally used maps as a source of information about places. We can now use a range of technology to help us find places, eg satellite navigation, GPS (global positioning systems) and GIS (geographical information systems) on our computers or mobile phones.

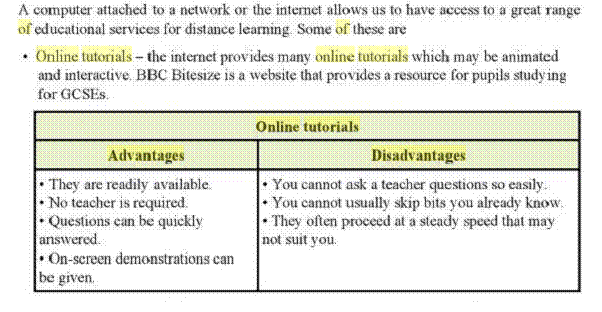
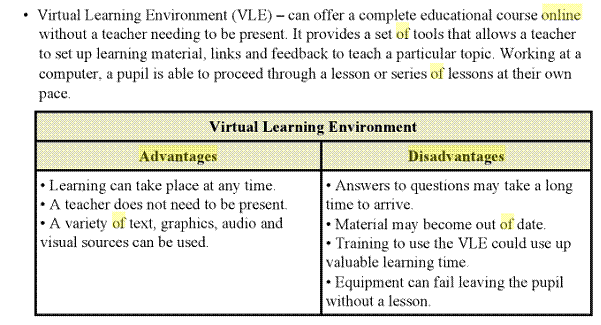
Online tutorials
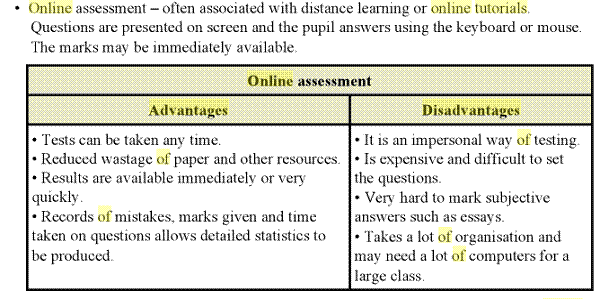
Online assessment and VLE (virtual learning environment
Video conferencing
Video conferencing means using computers to provide a video-link between two or more people. Instead of just talking to someone by telephone, you are able to see them as well.
Equipment
The following is needed to take part in a video conference call:
a computer
a web cam
a microphone (most webcams have a microphone built-in)
speakers
broadband Internet access
video conferencing software
It is possible to buy a special video conferencing machine just for this purpose.
Advantages of video conferencing
Meetings can take place without leaving the office.
Travel costs and the time taken to travel can be reduced significantly.
Meetings can be called instantly worldwide with little notice.
Delegates can still attend meetings even if they are physically unable to.
Disadvantages of video conferencing
May not be as productive as a discussion around a table.
Confidential documents may need to be viewed and signed in person.
There will always be times when you need to be able to meet face to face.
Chapter 10 : Improving ICT and GCSE ICT and Computer Science Practical Work
The general aim of ICT practical work is to prove skills have reached a certain level in:
Organising files and folders
E-mailing
Communicating Information
Handing data
Modelling
Specifically for GCSE short course:
3. Above should use all of Word, Mail Merge, Publisher and PowerPoint, XL and Access
Specifically for GCSE Long Course:
3. Also Includes Animation and Webpage creation. Also includes been able to comment on and criticise the web pages of others.
For Computer Science the aim of your practical work is to prove you can learn something about computer coding (programming) and start to experiment by modifying pre-existing code and eventually writing code of your own.
For beginners the programme languages available are:
Logo
Simple
Microsoft Small Basic
Web page creation using HTML
Specifically for GCSE the languages to be used are:
HTML
Small Basic
Green-foot Games Platform ( overlies JAVA)
Documenting your work in ICT and Computer Science (all levels)
This is essential and must be done in three ways:
Saving in your personal folder
Writing details of what you do in your ICT books ( not needed for GCSE but you will need to write a formative and summative assessment of your final project in Word)
Taking screenshot evidence using magnifier and paint to label or illustrate where appropriate
(3) Above is essential for GCSE ICT and for any interfaces you create in Computer Science.
Chapter 11 : Some Miscellaneous Further Definitions

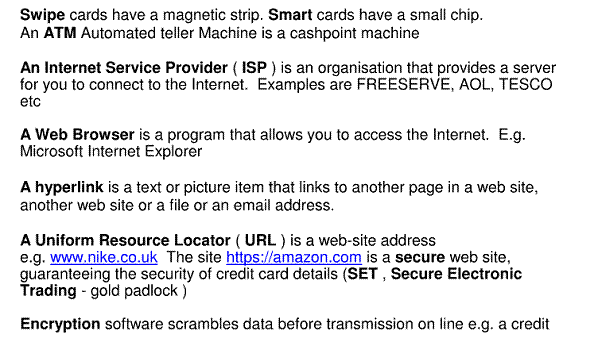

Fibre optic Broadband : line speed up to 70 Mbps only limited by fibre to copper converter as cable enters your house or green converter box in street.


· Never agree to meet a stranger unless with a parent/teacher/guardian and in a busy public place.
· Think carefully about what images you send on 'snap chat'



Chapter 12 Online Booking Systems
Online Booking Systems are websites or other "interfaces" to a shared database. The database holds all of the information available to all users. Any changes to it are also shown to all users.
A popular application of online booking systems is for booking flights. Users can visit an airline web site and click on a link to show available flights. This runs a query on the central database:
The results of the query are then shown in a new web page. The user can book the flight directly by entering details in a form on the web page.
The details a user has entered then get transferred into the central database, which is updated to show the new reservation and prevent anyone else booking the same seat.
Online booking systems use real-time transaction processing to enable all users to see up-to-date information.
They also restrict changes to the database to ensure that only one person can change a record (e.g. book a particular seat) at any time.
· A number of other disadvantages exist with the use of online booking. Because of the need for exchanging sensitive personal data, such as home addresses and bank and credit card details, the online booking process is an attractive target for cyber criminals looking to steal this information. Fake websites created for the sole purpose of stealing personal information is also an ever-present danger. Plus, as individuals don't have another individual to deal with in the booking process, it is left to them to read and understand the often complicated terms and conditions.
Chapter 13 Payroll Systems
At the end of each pay period, businesses need to pay their employees.
A payroll system uses a computer to calculate the wages of each employee, print out pay-slips and record the information for accounting purposes.
Input may come from a database of employees details (salaries, pay rates, bonus rates, etc.) or timesheets.
If employees are paid hourly, timesheets are used to input and validate the hours worked including any overtime (possibly using OMR or OCR techniques).
Validation: A range check could be used on the number of hours worked.
|
The Payroll Process |
The computer in charge of payroll needs to calculate:
the gross amount earned by each employee
any bonuses
any deductions such as tax, national insurance
the net amount earned by each employee.
Output: The computer would need to:
print pay-slips with amounts and deductions (using pre-printed stationery)
update the employee database
output details of payments to BACS (Bankers Automated Clearing Service) to pay money directly into employees' bank accounts.
print summary reports.
|
The Payroll Database |
A Payroll system is usually run as a batch processing system. Data may be entered for a number of departments or branches of a company and then the processing is done when all the data has been collected.
As there is no urgency for the output, the payroll processing may be run at off-peak times (e.g. overnight).
The database of the employees and the timesheets will need to be kept secure from unauthorised access - employees must not be able to alter their data!
The employee database is updated in the payroll process. A backup copy of the database is made before this is done.
The new database is called the son and the backup is the father. Previous generations of backups are referred to as grandfather, etc.
Chapter 14 Spreadsheets
Spreadsheets are a type of software for handling large amounts of data, often numerical. They consist of a grid of cells, although a spreadsheet files often contain more than one sheet.
A cell is where a row and column cross to make a box for you to enter data in.
Rows go horizontally across the screen.
Columns go vertically down the screen.
A cell gets its name from the column and row it's in. For example, A6 (Column A, Row 6).
In the same way that each field in a database can only hold one type of data, each cell in a spreadsheet can only deal with one type of data at a time.
For example, it is not possible to enter text and numbers in the same cell, and then be able to use the number in a calculation. The entire contents of the cell would be treated as text.
Spreadsheets are widely used because they allow you to use formulas to perform repetitive calculations. Formulas use cell names to perform calculations.
Answer to formulas will change when values in the cells it refers to change. This makes a spreadsheet dynamic and powerful.
SPREADSHEET FORMULAE
There are two ways of using cells in formulas: relative and absolute.
Relative references (to cells) change when a formula is moved to another cell. This is a powerful feature as it saves you having to work out a different formula for an identical calculation.
Absolute references to cells will always refer to exactly the same cell, even if the entire formula is moved or copied to another cell. This is powerful: change one cell's value and see its impact!
There are two main types of formula that you can use in a spreadsheet: logic and mathematical functions, although they are not the only types.
Logic functions help the spreadsheet decide how to act. For example, the IF function. Mathematical functions use data in the spreadsheet to calculate numerical answers. For example, the SUM function.
Spreadsheet software can display information in a variety of different formats including as a table, as a graph or as a chart.
Many spreadsheets will allow you to create graphs that automatically reflect changes to numbers in the spreadsheet.
Spreadsheets are often used in business as models to predict what might happen in the real-world.
The simplest models are used to produce a break-even analysis for new businesses. The spreadsheet predicts when the profit made by a business is exactly zero.
|
Spreadsheet Import/Export |
Spreadsheets also allow you to import data from and export data to other programs.
This is done by saving work in a format that both programs can understand.
A popular file type for spreadsheets is CSV (Comma Separated Variable), which transfers only the actual data without formatting.
Spreadsheets are programs that display data in grids of cells: columns and rows help you organise it.
Cells can only have one type of data entered into them.
Cells can have formulas in them which do calculations using data in other cells, e.g. adding up or averaging columns of numbers.
Formulas can use references to cells that are relative (will change if moved to another cell) or absolute (fixed).
Spreadhseets can analyse data to display graphs, charts and tables.
They can be used to model real life situations, such as how much profit a company can expect to make.
Spreadsheets can import or export data to other programs, with the CSV format being quite popular for this purpose.
Here is a quick list of some common Spreadsheet terms: A handy tool for those new to using a spreadsheet program like Excel or Microsoft Works.
1. Active Cell
In
an Excel worksheet,
each small rectangle or box is known as a cell.
The active
cell is
the cell surrounded by a black border. The black border is referred
to as the active
cell highlight
Data can
only be entered into the active cell.
Even if more than
one cell is selected, there is still only one active cell.
Use
the mouse pointer or the arrow keys on the keyboard to move the
active cell highlight from one cell to another.
It is
also known As the Current
Cell.
A
cell reference identifies the location a cell or
group of cells in the spreadsheet.
A cell reference
consists of the column letter
and the row number
that intersect at the cell's location. Note that when listing a cell
reference, the column letter is always listed first.
The
current cell reference can always be found in the Name
Box (see
below).
In some spreadsheet programs, a cell reference
is referred to as a cell
address.
3. Data
Data
is information that is stored in a spreadsheet program.
Data
is stored in the individual cells of a worksheet. Only one piece of
data is stored in each cell.
In addition to being stored
in the spreadsheet, the data can be used in calculations, displayed
in graphs, or sorted and filtered to find specific
information.
There are three types of data in Excel:
values, labels, and dates/times.
4. Formula
A
spreadsheet formula is a mathematical equation that will calculate a
result.
Examples of simple formulas : =
A3 - C6 / D2 or =
( B4 + B5 ) * E7
In
spreadsheet formulas, normally we use the cell
reference of
the data
rather
than the data itself.
In Excel, formulas begin with an
equal ( = ) sign.
Alternate Spellings: formulae
5. Function
A
function is a preset formula.
Like
formulas, functions in Excel begin with the equal sign ( = ) followed
by the function’s name and its arguments.
The
function name tells Excel what calculation to perform. The arguments
are contained inside round brackets and tell Excel what dataor
other information to use in the calculation.
For
example, the SUM function is one of the most commonly used functions
in Excel. It is used to add together the data in selected cells.
The SUM function is written as -
= SUM ( D1 : D6
)
Here the function adds the contents of cells D1 to D6
and stores the answer in cell D7.
Chapter 15 Video conferencing
Video conferencing means using computers to provide a video-link between two or more people. Instead of just talking to someone by telephone, you are able to see them as well.
Although it has important uses in distance education it is these days equally important in politics, business and for news media.
Equipment
The following is needed to take part in a video conference call:
a computer
a web cam
a microphone (most webcams have a microphone built-in)
speakers
broadband Internet access
video conferencing software
The simplest form of video conferencing is SKYPE and more recently Microsoft Lync 2013 which is a business oriented platform.
It
is also possible to buy a special video conferencing machine
for HD
peer to peer videoconferencing
which can be done totally protected by firewalls and on company
intranets.

Advantages of video conferencing
Meetings can take place without leaving the office.
Travel costs and the time taken to travel can be reduced significantly.
Meetings can be called instantly worldwide with little notice.
Delegates can still attend meetings even if they are physically unable to.
Disadvantages of video conferencing
May not be as productive as a discussion around a table.
Confidential documents may need to be viewed and signed in person.
On some paths, packet loss can result in drop outs and temporary loss of facial features or lip-sync.
If both ends of the VC circuit have very different VC standards or line speeds then a special Third Party link provider such as JANET Video Conferencing may be required.
There will always be times when you need to be able to meet face to face.
CHAPTER 16 : LATEST CHANGES MORE MODERN ICT STUFF NOW IN MOST GCSE SYLLABUS'S INCLUDING WJEC
Basic phones
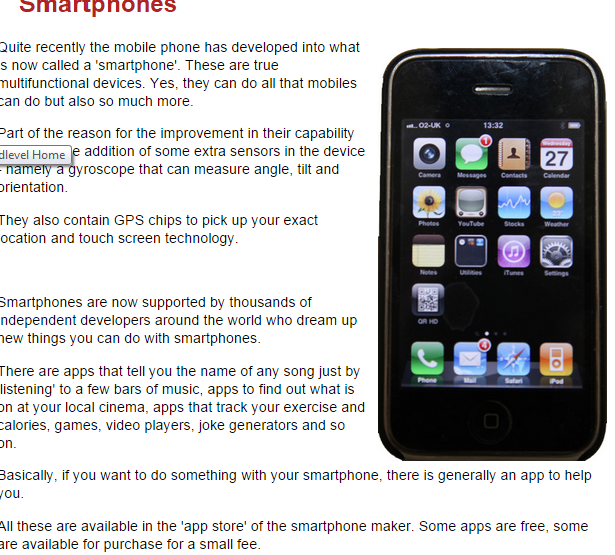
• Smartphones
• Specialist phones
Smartphones provide significantly greater functionality than basic
phones and are better suited for activities such as email, social
networking and surfing the web.
Specialist phones are ones designed for a very specific target market,
e.g. elderly people, people who are partially sighted, those operating
in challenging environments.
Phone peripherals
• Headsets (hands free)
• Removable storage
Televisions (including 3D TV)
• Projectors
• DVD players/recorders
• Blu-ray players
• Personal video recorders (PVR)
• Set-top boxes (STB)
• Media stations
• Sound systems (HiFi)
• Digital photo frames
Some devices may fall into multiple categories, e.g. a Sky+ box is both
a STB and a PVR. ( stb =set top box) pvr = personal video recorder)
Media stations are devices that provide video/audio to a television, e.g.
Apple TV. This could be by streaming from a remote source or from
local storage.
PMPS ( personal medial players )
Personal audio players
• Personal video players
• Portable media centres
• E-book readers
Personal media peripherals
• Speakers/headsets
Digital communications – device to device
Wired Device to PC etc. connections:
• USB cable
• USB 2.0, USB 3.0
• Firewire
• Thunderbolt
Firewire and Thunderbolt are high speed data ports.
Wired multimedia connections:
• Digital audio (e.g. SPDIF)
• HDMI
• Switches/splitters
HDMI (High Definition Multimedia Interface) transfers uncompressed
digital data. Typically, it is used for connecting high definition video
and audio devices.
A switch will allow multiple inputs to be output to one (or more)
device. A splitter will allow one input to be output to multiple devices.
Wireless connections:
• Infrared
• Bluetooth
• WiFi (Wireless Ethernet), WiFi Direct WiFi Direct is a way of allowing two devices to easily communicate/
transfer data.
Telecommunications:
• Mobile phone networks
(GPRS, GSM, EDGE, 3G, HSPA, 4G)
• Mobile phone bands (Dual, Tri, Quad)
• Landline phone network
Newer technologies (such as HSPA and 4G) greatly improve the speed
at which mobile phone networks provide online access.
Equipment needed to create a home network
• Modem
• Router
• Switch/hub/bridge
• Wireless base station/adapter
• Powerline networks
In many cases one device fulfils multiple functions. Types of modem
include ADSL, cable (fibre optic) and wireless broadband (3G).
A powerline network uses existing power points
In some countries PLC ( power line communications) also known as BPL ( Broad Band over Power line) are used but they are not presently licensed in the UK). However Power Companies do have a form of BPL for supervisory commands to SMART GRID systems.
Examples of Social networking/online workspaces
• Blogging
• Microblogging
• Public social networking
• Wikis
• Social bookmarking
• Online communities/virtual worlds
• Forums/message boards
• Web conferencing
Bluetooth

School MIS ( Management Information ) systems
These uses Database management and usually SQL server systems to
helps schools manage student registration and truancy, student performance, personalized learning, exam organisation, timetable construction, cover management and a range of other school activities
maintains real-time information to support schools in conducting regular and comprehensive self-evaluations, target resources, support personal development, promote achievements and share good practice
enables teachers to access information, analyse and input pupil data through the use of integrated desktop tools
provides web access through the Learning Gateway, which allows teachers and parents to access the data in database from home
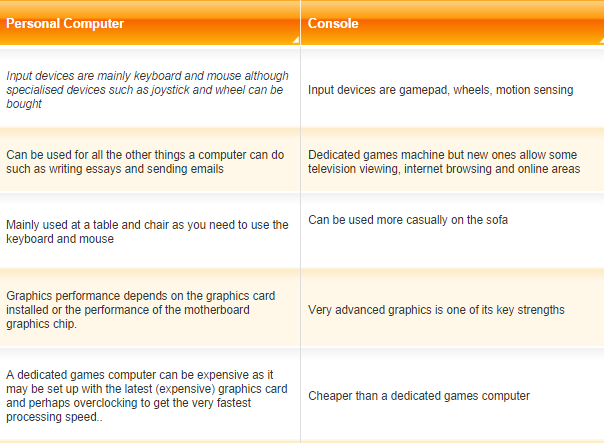
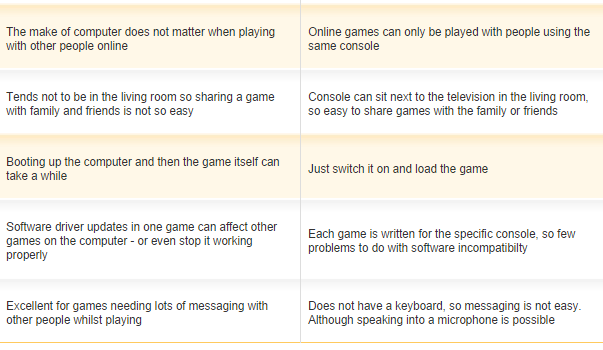
COMPUTER GAMING
List of Computer Input and Output Devices for the Disabled